U.S. export controls, as they stand, do not control the provision of cloud computing services and do not stop Chinese companies from accessing controlled chips via Cloud Service Providers (CSPs). In fact, a recent media report alleges that at least one problematic actor in China has found a way around the October 7, 2022 U.S. semiconductor export controls by accessing controlled chips via a CSP. Though this reporting does not provide evidence that the CSP in question was based outside of China, it may become common for Chinese firms to use foreign or overseas cloud services if the performance gap between locally available and foreign AI chips grows significantly due to export restrictions. If U.S. policymakers are interested in restricting this access, there are two potential pathways forward using export controls. The first is described in this post, and the second—which will focus on controlling access to compute for specific problematic actors and end-uses in China—will be outlined in a following post. In this post, we will outline Goal 1, highlight examples displaying how such controls might work, and discuss the advantages, disadvantages, and limitations of implementing controls in this manner.
Goal 1 is as follows:
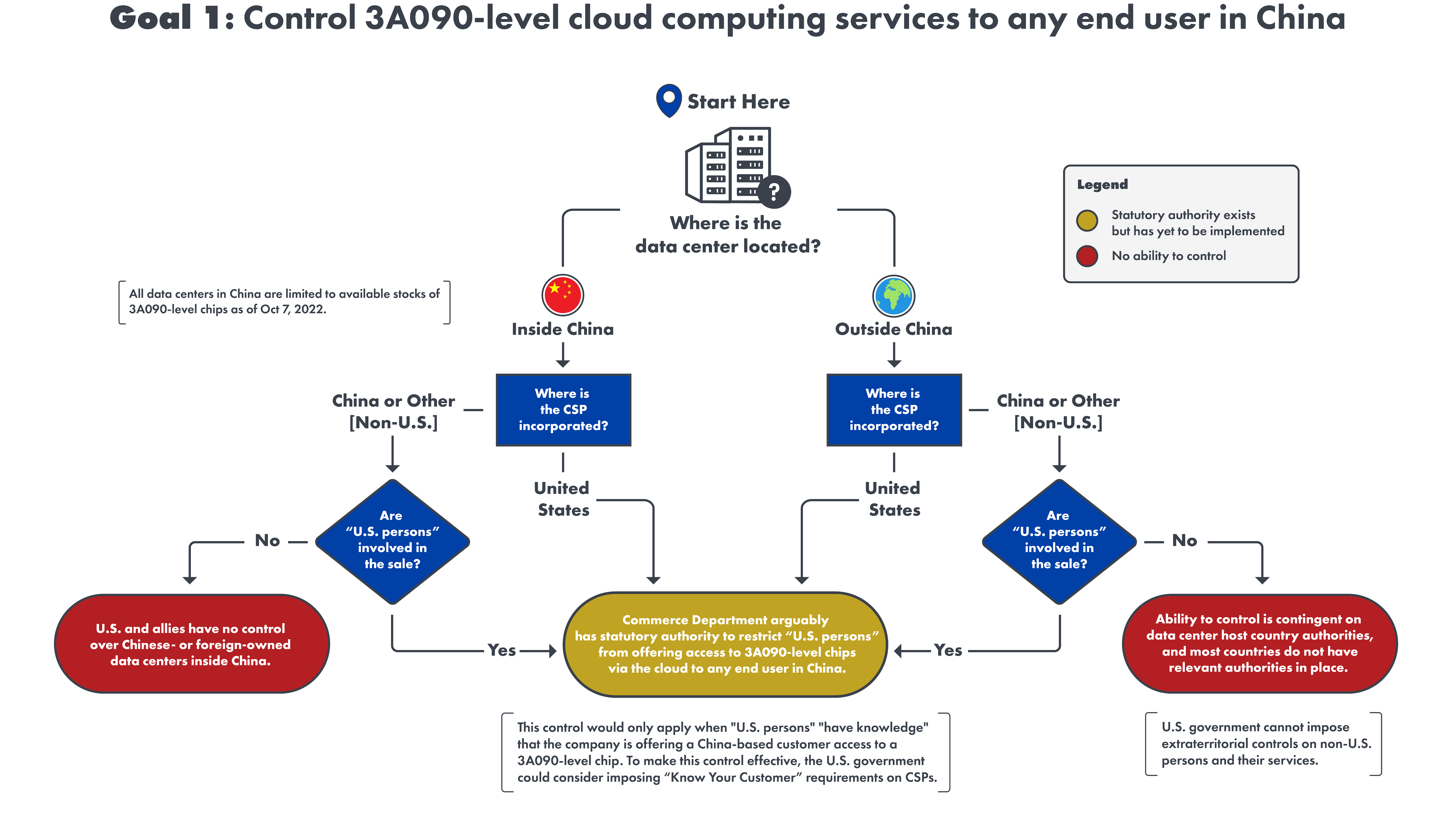
Control cloud computing services that provide a China-located user with access to an advanced chip controlled in the October 7 regulations (where “advanced” is defined under the parameters of Export Control Classification Numbers, or ECCNs, 3A090 and 4A090).
This post identifies situations where it appears U.S. export controls can be used to restrict cloud computing activities and situations where they cannot. As controls stand now, we do not recommend controlling access to cloud computing services for entities in China, because, based on our analysis, it does not appear feasible and may have adverse consequences. Forthcoming research from the Center for Security and Emerging Technology (CSET) and the Center for a New American Security (CNAS) will provide a more detailed analysis of this policy issue, outline additional recommendations, and consider policy options, such as making Infrastructure-as-a-Service (IaaS) directly controllable under the Export Administration Regulations (EAR) and implementing “Know Your Customer” rules for CSPs.
Understanding U.S. Policy: How Export Controls Do and Do Not Cover Cloud Computing
The October 7 export controls cover only the physical export (as well as the reexport and in-country transfer) of controlled items and not the provision of services that use those controlled items, including services like cloud computing.1
For cloud computing in particular, the Bureau of Industry and Security (BIS) at the Department of Commerce has taken the position that providing such capacity is a service and therefore not subject to the EAR. Moreover, BIS treats the user/customer of a cloud computing service—not the CSP—as the “exporter” in question. For these reasons, the EAR’s item-based controls, end use controls, and end user controls—each of which applies only to physical goods, software, and technology—do not control cloud computing services. This leaves one remaining option under the EAR: controls on the activities of “U.S. persons.”
To control the provision of cloud computing services under the EAR as it’s currently structured, U.S. policymakers must rely on existing and new “U.S. persons” controls. These controls allow the U.S. government to restrict “U.S. persons”—including U.S. citizens (wherever they are located around the world), permanent residents, U.S. companies, and any person located in the United States—from engaging in activities that “support” certain restricted activities. “Support,” in the context of “U.S. persons” controls, hinges on the “U.S. persons” having knowledge that their activities or services are in support of a controlled end use or for a controlled end user. Already highly complex as they stand, these controls are even more complicated in the context of controlling cloud computing services, which we will discuss in more detail below.
“U.S. persons” involved in the sale of cloud computing services are the only legal hook under the EAR that the U.S. government could use to control the provision of advanced cloud computing services to any end user in China. BIS arguably has the statutory authority to expand “U.S. persons” controls to restrict “U.S. persons” from providing services using controlled advanced chips to entities in China.2
However, this authority has yet to be implemented in the EAR.
The flowcharts below demonstrate how “U.S. persons” involved in the sale of cloud computing services are the legal hook for the U.S. government to control the provision of advanced cloud computing services to any end user in China.
Goal 1: Control cloud computing services that provide a China-located user with access to an advanced chip controlled in the October 7 regulations (where “advanced” is defined under the parameters of ECCNs 3A090 and 4A090).
To align with the objectives laid out in the October 7 rules, Goal 1 assumes that U.S. policymakers are concerned about any user in China gaining access to the most advanced AI chips—either by physically purchasing them or accessing them through cloud computing services. Based on the rationale in the October 7 controls, we assume that, due to policies like China’s military-civil fusion strategy, the risk of diversion to the military in cases involving advanced technology is high.
Let’s consider a few examples of how U.S. regulations could be shaped to achieve this goal. We will refer to hypothetical CSPs based on their country of incorporation.
Data Centers inside China
Example: U.S. CSP-owned data center in China
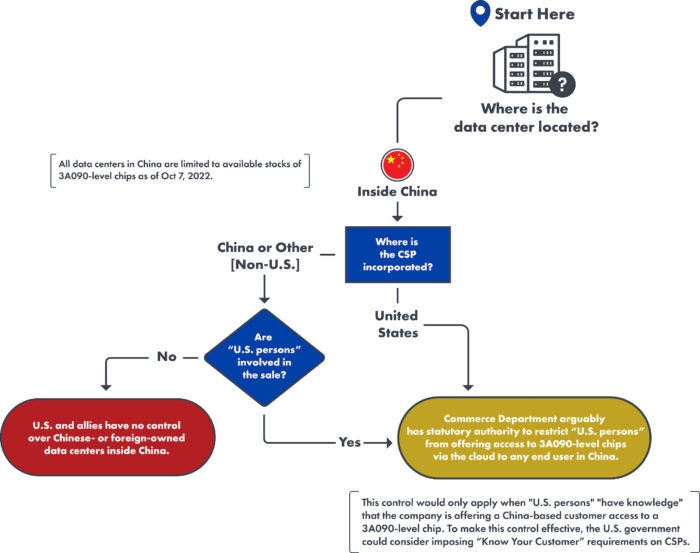
- The export of advanced chips to any China-located data center, including those owned by a U.S. CSP, is already restricted. All data centers in China are limited to using available stocks of chips acquired prior to October 7, 2022 (or otherwise smuggled into China illegally).
- The ability to restrict the U.S. company from offering cloud computing services to an entity in China is dependent on whether “U.S. persons” are involved in the sale of cloud computing services.
- If “U.S. persons” (anywhere in the world) are involved, BIS arguably has the statutory authority to regulate that activity.
- If no “U.S. persons” are involved, then BIS currently has no means to further restrict this data center from offering services to other entities in China.
- As far as we know, the major U.S. CSPs (including but not limited to Amazon Web Services and Azure) operate in China through an “operating partner”, as required by China’s legal and regulatory regime. As such, it is difficult to determine the United States’ legal jurisdiction in this context. Much of it is dependent on the structure and legal agreements between CSPs and their partners in China.3
Data Centers outside China
Example: Chinese CSP-owned data center in the United States
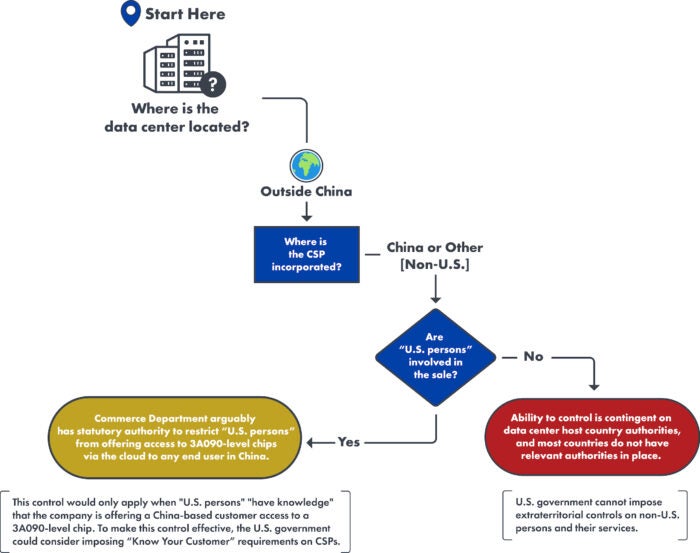
- U.S. export controls do not restrict a Chinese CSP-owned data center located in the United States from purchasing controlled advanced chips, because the chips in question are not being physically exported to China.
- This could apply to, for instance, an Alibaba Cloud data center located in Virginia or a Tencent Cloud data center in San Francisco.
- At the moment, Chinese cross-border data regulations incentivize Chinese entities to store data and train AI models inside China. However, if the gap in computing power between the U.S. and China grows over the next few years—due in part to the October 7 export controls—Chinese entities may seek out overseas data centers owned by Chinese CSPs, as these entities are most likely to fall under the jurisdiction of Chinese law, even extraterritorially.
- The ability to restrict the Chinese CSP-owned data center in the United States from offering cloud computing services to an entity in China is dependent on whether “U.S. persons” are involved in the sale of cloud computing services.
- Notably, any company (or data center) located in the United States is considered a “U.S. person.” If “U.S. persons” are involved in the sale, BIS arguably has the statutory authority to restrict these activities. However, this authority would likely require that either the sales team be located in the United States or that U.S. employees of the data center have knowledge of who is accessing controlled chips—the latter of which is unlikely.
- If no “U.S. persons” are involved, then the EAR provides no means to further restrict this data center from offering services to other entities in China.
Limitations and Conclusion for Goal 1
As demonstrated above, attempting to achieve this first goal is complex and comes with several significant limitations.
First, implementing “U.S. persons” controls to restrict access to advanced cloud computing services could put U.S. persons—both CSPs and individuals—at a disadvantage in the global cloud service industry. No other country has the equivalent of “U.S. persons” controls, so plurilateralizing U.S. policies in this context would require a massive overhaul of allied export control authorities. There are also no international harmonized standards or governance policies related to cloud computing, which makes plurilateral action even more difficult. In the absence of any plurilateral arrangements, the United States can only restrict access to advanced cloud computing services when “U.S. persons” are involved in the sale of the service. This could incentivize foreign CSPs to remove “U.S. persons” from their China sales teams to avoid U.S. licensing requirements. Not only do these factors limit the effectiveness of achieving the stated objective, but they would also lead U.S. companies to disproportionately bear the cost of a new control.
Second, as U.S. policy stands now, CSPs are not required to collect information on their customers’ location or the chips to which their customers have access—information that would be needed to control the activities of “U.S. persons” as specified in the above goal. For example, even if BIS implemented a “U.S. persons” control on advanced cloud computing services tomorrow (Goal 1), providers would only be liable if BIS discovered after-the-fact that they had knowledge of providing a controlled cloud computing service into China. Until this changes—perhaps through new “Know Your Customer” requirements—controls on cloud computing services will likely be ineffective. Future work from CSET and CNAS will go deeper on this issue.
Lastly, even with the implementation of new controls on “U.S. persons” and complementary “Know Your Customer” requirements, Chinese entities could possibly achieve similar performance levels in aggregate by purchasing or renting (via cloud computing services) chips that are not covered by U.S. export controls. In the wake of the October 7 controls, U.S. policymakers should continue to monitor the ways in which Chinese entities can continue to access advanced compute via alternative means like cloud computing services, as these access points could provide opportunities to craft more fine-grained controls, as opposed to broader bans on additional categories of physical chips.
In conclusion, although arguably possible, using the EAR as it stands to control the sale of advanced cloud computing services to Chinese users is fraught with potential loopholes. To make “U.S. persons” controls effective in the pursuit of this objective, the U.S. government would need to place new due diligence requirements on U.S. CSPs, which we will consider in an upcoming report.
Part II of this series can be found here.
Notes
- China in this context includes both Hong Kong and Macau.
- As of April 2023, it is difficult to determine how China’s cross-border data flow regulations will be implemented. We assume that the regulations will incentivize Chinese entities to access cloud computing services via domestic Chinese data centers.
- Foreign subsidiaries of U.S. CSPs are not directly subject to U.S. persons controls because “U.S. persons” as defined by the Export Administration Regulations (EAR), does not include separately established foreign subsidiaries of U.S. firms. However, the activities of U.S. person employees, managers, and directors of the subsidiary would be subject to EAR 744.6. This also applies to U.S. CSPs operating outside of China.
- As far as we know, the major U.S. CSPs (including but not limited to AWS and Azure) operate in China via one or more China-based subsidiaries.
- As explained in Supplement No. 3 to Part 732 of the EAR, individuals and firms must satisfy due diligence requirements when exporting items subject to the EAR. Since services—including cloud computing—are not subject to the EAR, they are exempt from these requirements.
- CSPs are not required to collect information on their customers’ location or the chips that customers can access—knowledge that would be needed to control the activities of U.S. persons as specified in Goal 1. Until this changes, controls on cloud computing services are likely to be ineffective.
- Assuming that the CSP is not also transferring controlled data or software, the act of providing access to a cloud server is considered a service and is therefore not subject to the EAR.
- To achieve this goal, BIS could arguably use its statutory authority to create regulations to restrict U.S. person services using 3A090 products, including via the cloud, to any end user in China. This authority is strengthened by the December 2022 NDAA, which gives BIS the authority to restrict the activities of U.S. persons in support of foreign military, security, or intelligence services. In practice, BIS could make adjustments to EAR 744.6 to restrict the activities of U.S. persons in support of the design, “development,” “production,” operation, installation (including on-site installation), maintenance (checking), repair, overhaul, or refurbishing, of any item in or by the PRC, if the provision of such support involves the use of an item meeting the parameters of 3A090 or 4A090.
- If the CSP’s China sales operations most closely resemble a foreign branch then we would treat it as a U.S.-incorporated CSP, and BIS would arguably have the statutory authority to restrict the CSP from offering access to advanced chips via the cloud to any end user in China. If—based on the structure of the partnership—the CSP’s China sales team should not be treated as a U.S.-incorporated CSP, individual “U.S. persons” employees involved in the sale would be a potential hook for BIS to control the provision of cloud computing services.